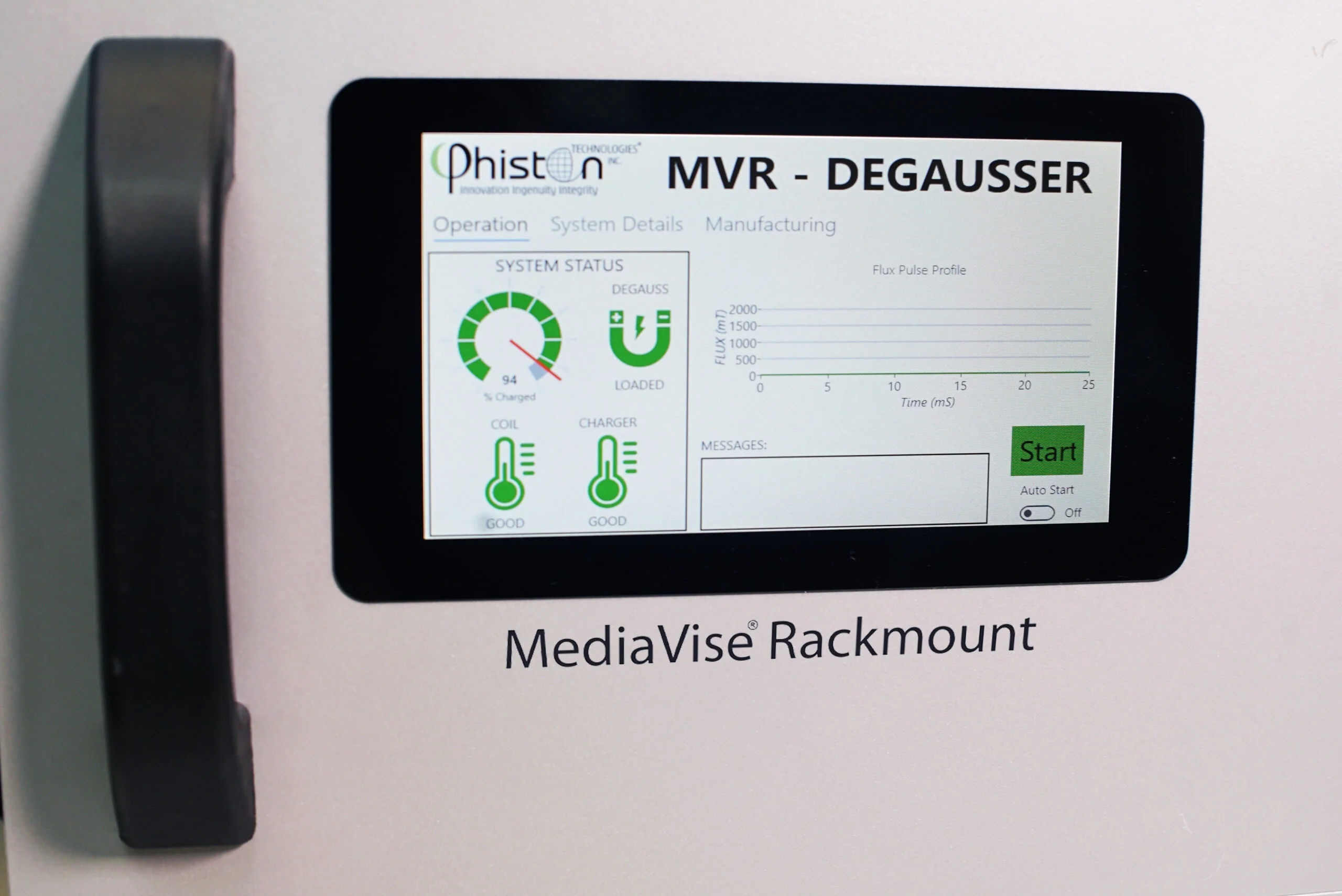
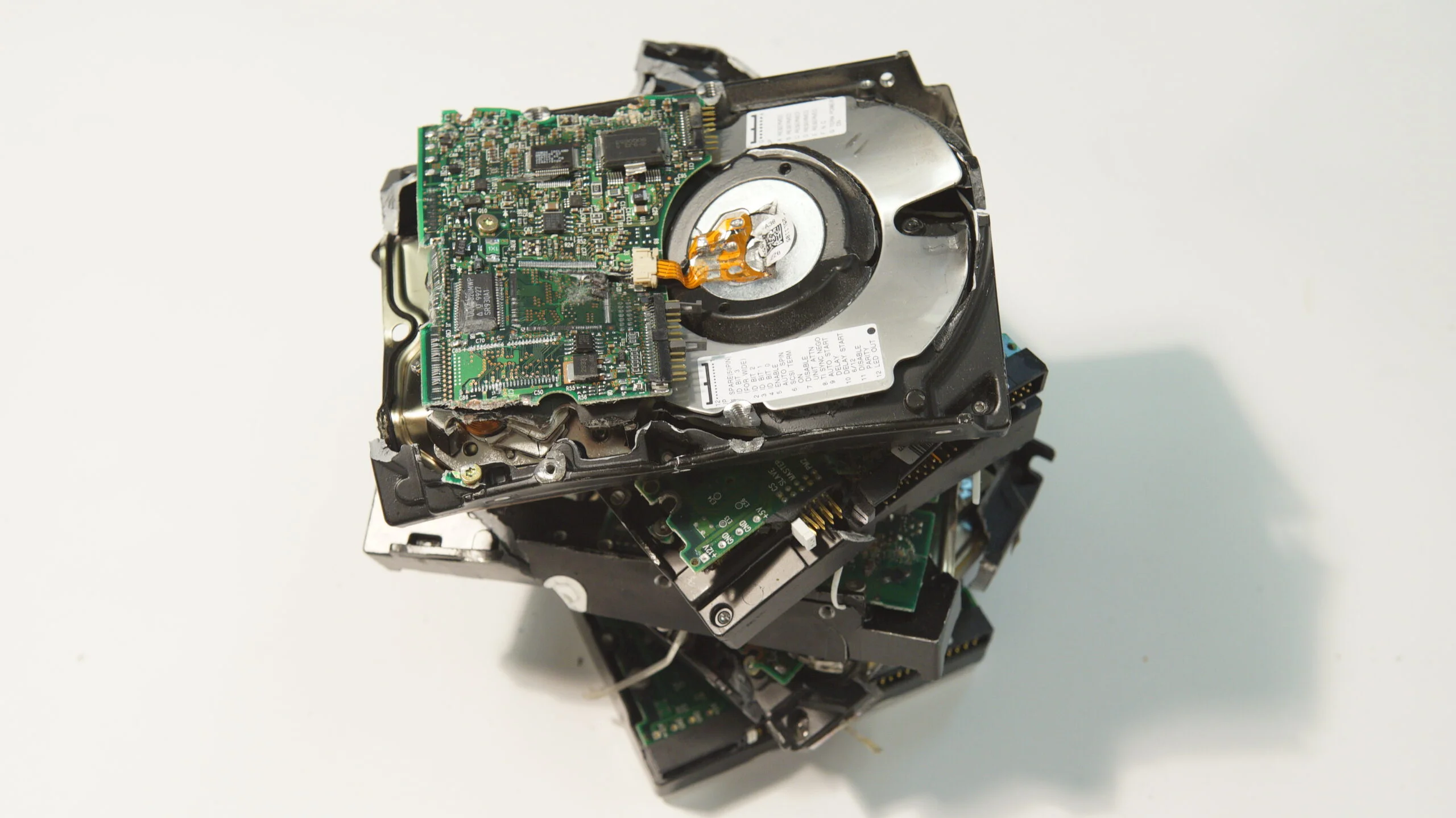
ISO27001 Certification and Risk Assessment
ISO 27001 Certification Organizations of all sizes are facing a constant stream of threats. In the last few years alone, millions of users had their information stolen (for example, at Equifax in 2017, where a breach exposed names, social security numbers, and even customer credit cards). The average breach costs a company about $1.6M (IBM […]
ISO27001 Certification and Risk Assessment Read More »